Removing Spyware
In this context, spyware refers to anything that doesn’t belong,
such as viruses, adware, malware, trojans, backdoors, etc. It can also
include software that was installed as part of a bundle, but not needed, like
tray icons for RealPlayer and QuickTime. Below is a list of suggestions
in no particular order. Some of the suggestions require more experience
than others, but may be necessary when removing more pernicious spyware.
Many of the steps below involve deleting files. To ensure that you can
see hidden files, go to My Computer, Tools, Folder Options, View, check ‘show
hidden files and folders’, and uncheck ‘Hide extensions for known file types’
and ‘Hide protected operating system files’. When done troubleshooting,
change these settings back to their original values.
1. Install Symantec Antivirus
version 10
Version 10 includes spyware removal and proactive spyware prevention. If
you currently have version 9 installed, you should be able to upgrade to
version 10 just by running the version 10 installer. If you have a version
earlier than 9, you will need to take the following steps: In the Add/Remove
Programs control panel, uninstall all Norton and Symantec products. Then
uninstall LiveUpdate. Then delete the folder “C:\Documents and Settings\All
Users\Application Data\Symantec” (The ‘Application Data’ folder is a hidden
folder, so you’ll need to have turned on viewing of hidden files and folders as
described in the second paragraph on this page). Reboot, download version 10
from http://www.cmu.edu/myandrew, install
it, and do a full scan.
2.
Run Ad-aware SE Personal
Ad-aware scans for and removes most known types of adware, but doesn’t
remove viruses or most backdoors. Download the free version from http://www.lavasoftusa.com/software/adaware/.
(There is no need to get the Plus or Professional version.) The first
time you run Ad-aware, click the ‘check for updates now’ link on the bottom
right to get the latest reference file. Another good product is Spybot Search &
Destroy, downloadable from http://www.safer-networking.org/en/download/index.html.
3.
Remove suspicious Internet Explorer plugins.
If you’re running Windows XP with Service Pack 2 (SP2), you can view and delete
plugins from within IE via Tools, Manage Add-ons. If you’re pre-XPSP2, or
want to do a more thorough removal, you can delete plugins manually by deleting
the contents of the folder "c:\windows\downloaded program files".
If this doesn’t fix Internet Explorer problems, you can use an alternate web
browser to circumvent the IE problems, such as Firefox (http://www.mozilla.org/products/firefox
). In general, it’s recommended to avoid using IE entirely in order to
limit vulnerabilities to any exploits discovered in IE-specific technologies
like ActiveX.
4.
Remove items from the Startup folder.
These are programs that start when you log into Windows.
Navigate to the Startup folder in the Start menu (Start menu, All Programs,
Startup), rightclick on each item in the startup folder and select
‘delete’. It’s usually safe to delete everything there. If you use
Mulberry you should leave Leash Ticket Manager. (If you’re using an
older version of Mulberry, you might see “kclient” instead.)
5.
Turn off suspicious services.
Services are programs that run all the time, even when no one is logged into
the machine.
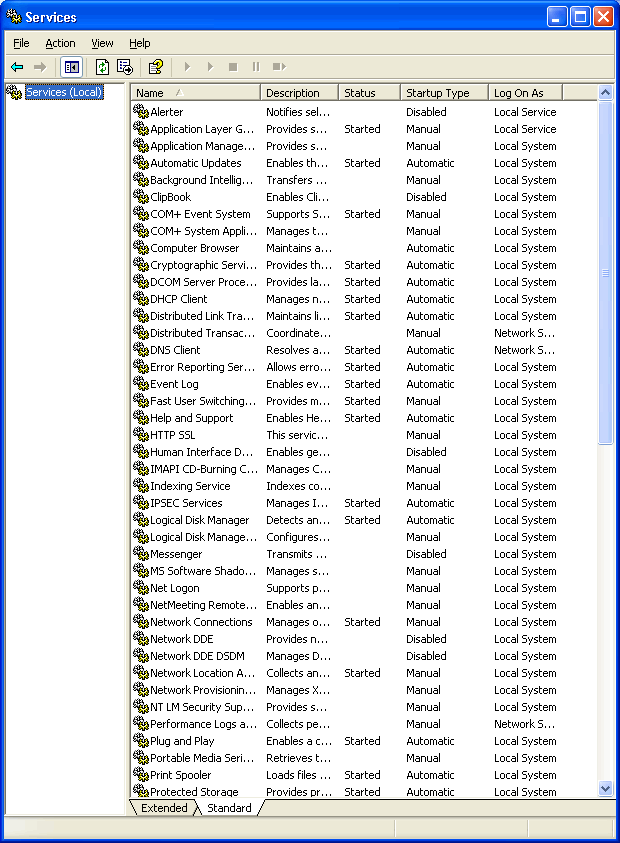
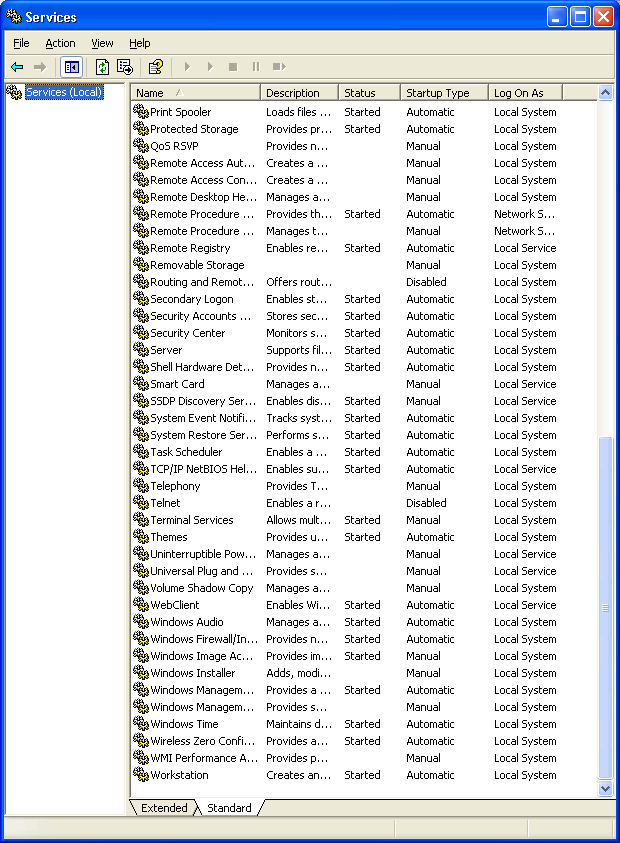
To view your services, go to the Start menu, Run, and type services.msc.
Below is a list of all of the services (shown across two screenshots due to
length) and their default setting on a newly installed Windows XP
machine. It’s usually safe (and a good idea) to disable any service not
appearing on this list. In particular, look for and disable any service
that has FTP in the name.
6.
Remove items from the Run section of the registry.
The registry is a database of settings/preferences for applications and the
operating system itself. The ‘Run’ section of the registry contains a
list of what programs start when a user logs in.
To view the registry, go to the Start menu, Run, and type regedit. There
are two separate Run sections- one for all users, and one for the currently
logged in user. To view the first, navigate to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. To view
the second, navigate to
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. The
beginnings of the two different sections are often abbreviated as HKLM and
HKCU.
Usually you can tell what an entry is by its path, such as vptray running from
c:\progra~1\symant~1\..., indicating its part of Symantec Antivirus. If
an item doesn’t have a path, there’s a good chance it’s a virus or
adware. The best approach is to research each item before deleting it, as
deleting legitimate items can make you lose functionality (ex: unable to burn
CDs, use laptop special keys, etc.). One approach is to select the Run
folder, then go to File, Export to save a copy of the Run section to a file
that can be imported again later if something gets deleted that shouldn’t be.
Other sections to scrutinize include
{HKLM,HKCU}\software\microsoft\windowsNT\currentversion\windows and
HKCR\exefile\shell\open\command, although these are less commonly compromised
and could be compromised in a variety of ways that are beyond the scope of this
document. Comparing those sections to another machine might turn up
suspicious discrepancies though.
* Editing the registry is dangerous… only attempt
this step if you’re fairly familiar with the operating system, or as a last
resort, or if you have your data backed up, and/or are willing to risk not
being able to boot your PC. *
7.
Delete the Prefetch files.
Windows XP speeds loading of frequently used applications by saving parts of
them to the directory %systemroot%/Prefetch (%systemroot% is a shortcut for the
directory Windows is installed in, such as C:\Windows) and loading those files
when the computer boots. Those files might become corrupt or compromised
even if the originals they were copied from are still good. It’s safe to
delete all files from the Prefetch directory, which will cause Windows to
recreate new prefetch files as needed from the originals.
To delete the files, go to the Start menu, Run, type %systemroot%/prefetch, and
delete all the files.
8.
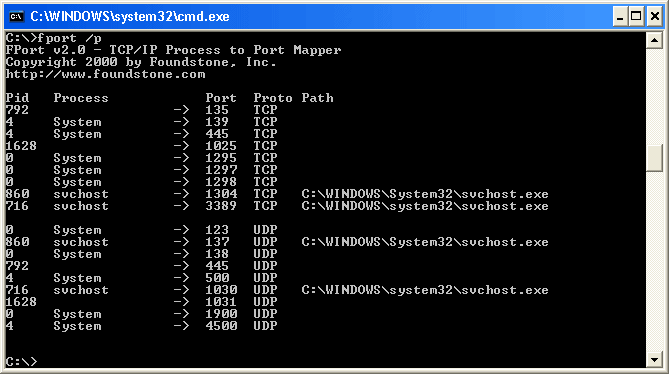
Run Fport
Fport is a free utility to list open ports on your computer. Network
communication uses different ports for different services, like port 80 for web
pages and port 25 for sending email. Listing what ports your computer is
‘listening’ on can uncover certain types of spyware.
Copy fport from \\chemserv.chem.cmu.edu\software\miscellaneous
and put it in your %systemroot% directory. Close all other programs, then
go to the Start menu, Run, type ‘cmd’ to bring up a command window, and run
‘fport /p’ in that window. Below is the output of fport on a clean XP
machine. Any items that your computer has in addition to these should be
scrutinized.
9.
Run HiJackThis
HiJackThis is a powerful utility that list many different types of startup
items in one place. Using HiJackThis does require some expertise and
experience to properly identify which items belong and which don’t.
Create a folder “C:\Program Files\HiJackThis” and copy HiJackThis.exe from \\chemserv.chem.cmu.edu\software\miscellaneous
into that folder. Launch HiJackThis from the “C:\Program
Files\HiJackThis” folder and select ‘Do a system scan only’. Below is a
list of the results from a clean XP machine.
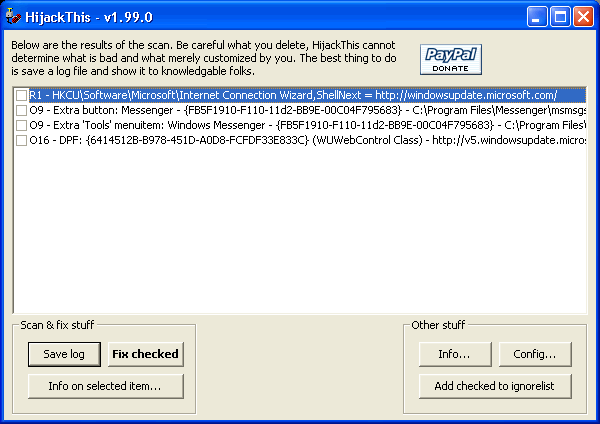
Your computer may have many more items listed, most or all of which are
legitimate. BHO and DPF entries are ‘Browser Helper Objects’ and
‘Downloaded Program Files’. Usually all items are safe to delete, but you
may lose desired functionality if you delete all of them. The best way to
proceed is to determine what each object is individually, such as searching
google for each filename. HiJackThis also looks for browser homepages and
search/security settings set to non-standard values. Selecting an object
and clicking ‘Fix checked’ will either delete the item or change the setting
back its default value, whichever is applicable.
A complete tutorial for using HiJackThis can be found at http://www.spywareinfo.com/~merijn/htlogtutorial.html.
Log files from hijackthis can also be analyzed automatically at this site: http://hijackthis.de.
10. Delete Hidden Data Streams
With the NTFS file system, a file can have several ‘forks’. Almost all
files just have a ‘data fork’, which is what’s displayed by My Computer, but
they can have other forks that are normally completely hidden.
To scan for these hidden data streams, launch HiJackThis, select ‘None of the
above, just start the program’, click Config, Misc Tools, Open ADS Spy, and
Scan. Delete all files that show up in this scan.
Click the Back button under Other Stuff to get back to the normal HiJackThis
scan screen if desired.
11. Boot
into Safe Mode
Safe Mode loads only the most basic hardware drivers and skips most of the
extra startup steps. Often it’s the case that pernicious spyware will
monitor for its own deletion and then replace itself on the hard drive.
The other frequent scenario is that suspect file that you want to delete will
be actively in use by the spyware and the operating system won’t allow you to
delete it. Booting into Safe Mode greatly increases the chances that you
can boot in a way where the spyware won’t be launched, which will allow you to
delete the suspect files. If any of the steps above seem to have
problems, try the steps again from Safe Mode.
To boot into Safe Mode, press F8 after the computer’s POST (Power On Self Test-
where it checks memory and connected drives) and before the Windows splash
screen appears. If the timing is correct, you’ll see a text menu of boot
options which includes a Safe Mode option. If you’re unable to get the
menu, you can use the program msconfig (XP only. Start menu, Run,
msconfig) to reboot in diagnostics mode.
In some cases you may even need to boot into ‘Safe Mode, Command Prompt Only’
in order to prevent explore.exe from running. Explore.exe is the program
that is the main interface to the computer, controlling the desktop, the Start
menu, the task bar, etc., not to be confused with iexplore.exe, the Internet
Explorer web browser. Some spyware integrates itself into explore.exe and
thus booting into Command Prompt Only is the only way to delete certain files.
12. Check
the hosts file
The file %systemroot%/system32/drivers/etc/hosts can be compromised to
trick your computer in visiting malicious sites. On a clean machine, the
only uncommented line is “127.0.0.1 localhost”. Some popup blockers may
add to this file by redirecting other sites to localhost. If any sites are
directed to anything other than localhost, the file is probably compromised and
should be replaced with a copy from another machine. You can use notepad
to edit the file, but be careful not to add a .txt extension to the filename.
13. Use
tasklist.exe
In XP, the program ‘tasklist /svc’ and other tasklist switches can be useful
for identifying which programs use which DLLs. Specifics are beyond the
scope of this document though.
14. Use
msconfig.exe
In XP, msconfig can be used to view/edit settings from several places.
15. Visit the Help Center
The Help Center (http://www.cmu.edu/computing/support)
has a large staff of individuals trained in removing spyware.